23andMe, and You, and Your Mama and Your Sister
On Oct. 1, 2023, a small percentage of 23AndMe user profile information was improperly accessed and downloaded from individual 23andMe.com accounts on its website. The company found out after an anonymous hacker began advertising “millions” of stolen genetic profiles that were supposedly from 23andMe customer accounts. The profiles included emails, photos, gender, date of birth […]
Highlights From Cybersecurity and Infrastructure Security Agency’s Cybersecurity Advisory
In my last rAVe column, I summarized some recent cyberattacks on MGM and Caesars’ casinos. In that article, I tried to drop some social engineering science and some lessons learned from Scattered Spider (aka 0ktapus, UNC3944, Starfraud, Scatter Swine, Muddled Libra and most recently, Octo Tempest). I warned #AVtweeps about their aggressive social engineering Tactics, […]
Social Engineering Safety Takeaways From MGM Resorts and Caesar’s Entertainment Cyberattacks
On Sept. 11, 2023, a number of MGM resorts and casinos were simultaneously disrupted by ransomware and data extortion attackers, costing the company $100 million, according to AP News. Caesar’s Entertainment was also attacked, which the Wall Street Journal reported resulted in the company paying roughly half of the $30 million demanded. The resorts and […]
Lessons From Uber: How NOT to Respond to a Cybersecurity Incident
After suffering a major data breach six years ago, you would think that a company like Uber would be ready for more cyberattacks, but here we are. How did we get here? [insert flashback music] It was late 2016. Cyberattackers quietly breached the security perimeter of Uber networks and accessed the personal data of 57 […]
It’s Not Just About Your SSN — It’s About Protecting Your PII
TL;DR Tech giant Samsung suffered two major data breaches this year. It alerted those customers who were affected. Now there’s a class-action lawsuit against the company. On Sept. 6, 2022, a class-action lawsuit was filed against Samsung Electronics America, Inc. (hereinafter “Defendant” and/or “Samsung”). Plaintiff Shelby Harmer and thousands of individuals (hereinafter referred to as […]
#HootHoot Meeting Owls Security Vulnerabilities Have Been Patched, Have Yours?
In January 2022, cybersecurity researchers at Modzero reported a handful of security vulnerabilities to Owl Labs regarding their 360-degree videoconferencing Meeting Owl, Meeting Owl Pro, Meeting Owl 3, and Whiteboard Owl. Owl Labs has since released patches for these vulnerabilities. (The below is the Meeting Owl 3, as shown at InfoComm 2022.) The security patches […]
SecuringAV: The iPhone Spyware Vulnerability
What YOU Can Do To Prevent Hackers From Hijacking Your Smart Device’s Microphone For each column in this series, rAVe writer Paul Konikowski takes a deeper dive into a recent security event or data breach, shedding light on supply chain vulnerabilities, infrastructure and cyber-physical security. OMG, did you watch the Apple “Unleashed” stream? No, not the […]
SecuringAV: The Colonial Pipeline Ransomware Cyberattack — Part 2
What motivates a hacker or group of cyberattackers? The answer is typically money. For each column in this series, rAVe writer Paul Konikowski takes a deeper dive into a recent security event or data breach, shedding light on supply chain vulnerabilities, infrastructure and cyber-physical security. The Colonial Pipeline ransomware attack in May of 2021 caused […]
SecuringAV: The Colonial Pipeline Ransomware Cyberattack — Part 1
Why did the pipeline get shut down if the hackers only attacked the business end? For each column in this series, rAVe writer Paul Konikowski takes a deeper dive into a recent security event or data breach, shedding light on supply chain vulnerabilities, infrastructure and cyber-physical security. By now, most people heard about the Colonial […]
SecuringAV: The Remote Desktop Attack on a Florida Water Treatment Plant
For each column in this series, rAVe writer Paul Konikowski takes a deeper dive into a recent security event or data breach, shedding light on supply chain vulnerabilities, infrastructure and cyber-physical security. In my last “SecuringAV” column about the Nashville Christmas morning bombing, I did my best to define what “infrastructure project” meant using the […]
SecuringAV: The Christmas Morning Bombing in Nashville
For each column in this series, rAVe writer Paul Konikowski takes a deeper dive into a recent security event or data breach, shedding light on supply chain vulnerabilities, infrastructure, and cyber-physical security. In my last SecuringAV column about the SolarWinds hack attack, I asked rAVe readers an open-ended question: If extremists think that Big Tech is […]
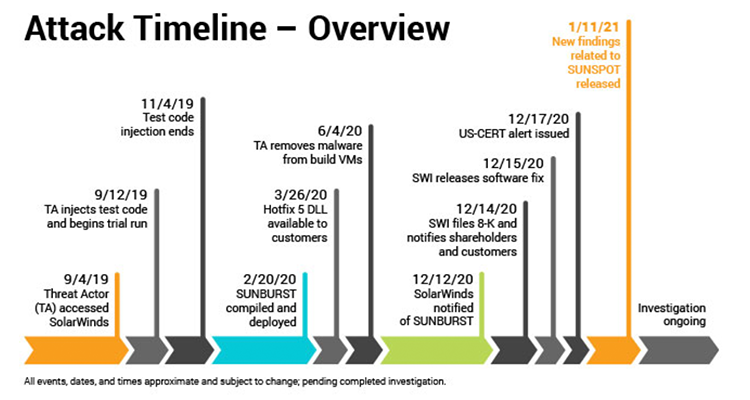
Securing AV: The SolarWinds Attack of 2020 (Actually 2019)
For each column in this series, rAVe writer Paul Konikowski takes a deeper dive into a recent security event or data breach, shedding light on supply chain vulnerabilities, infrastructure, and cyber-physical security. While most Americans are still processing the recent attack on the United States Capitol building, many cybersecurity researchers and professionals believe the real […]
Are We Gonna Talk About Zoom ‘Being on Probation’ for 20 Years by the FTC, or Nah?
So…are we gonna talk about Zoom “being on probation” for 20 years by the FTC, or nah? — Erica Williams (@haircutfw) November 13, 2020 On Nov. 9, 2020, the United States Federal Trade Commission announced a pending settlement with Zoom Video Communications, Inc. According to FTC Matter/File Number: 192 3167, “Zoom Video Communications, Inc. will […]
Updated: How Zoom’s Recent Success Has Put Them Square in the Security Spotlight
P.T. Barnum is credited for saying,”There’s no such thing as bad publicity.” You may have heard other variations of this old saying, such as “There’s no such thing as bad press.” Does this apply to recent headlines about Zoom? If you have lost track, I will do my best to summarize and put it all […]