Highlights From Cybersecurity and Infrastructure Security Agency’s Cybersecurity Advisory

In my last rAVe column, I summarized some recent cyberattacks on MGM and Caesars’ casinos. In that article, I tried to drop some social engineering science and some lessons learned from Scattered Spider (aka 0ktapus, UNC3944, Starfraud, Scatter Swine, Muddled Libra and most recently, Octo Tempest). I warned #AVtweeps about their aggressive social engineering Tactics, Techniques and Procedures (TTPs). Well, as it turns out, I’m not the only one getting arachnophobia about Scattered Spider.
On Nov. 15, Reuters reported that the FBI struggled to disrupt dangerous casino hacking gang Scattered Spider. Michael Sentonas, president of CrowdStrike, was quoted as saying, “For such a small group, they [Scattered Spider] are absolutely causing havoc.”
On Nov. 16, 2023, the FBI and the Cybersecurity and Infrastructure Security Agency (CISA) dropped its own science, releasing an advisory on Scattered Spider. I’ve pulled together some highlights from the advisory, which you can follow to protect you and your organization from hackers like this group.
One of the most valuable takeaways is this list of normally legitimate tools used by the group. Each of these on their own is not suspect, but a combination of them is, and their usage should be closely monitored:
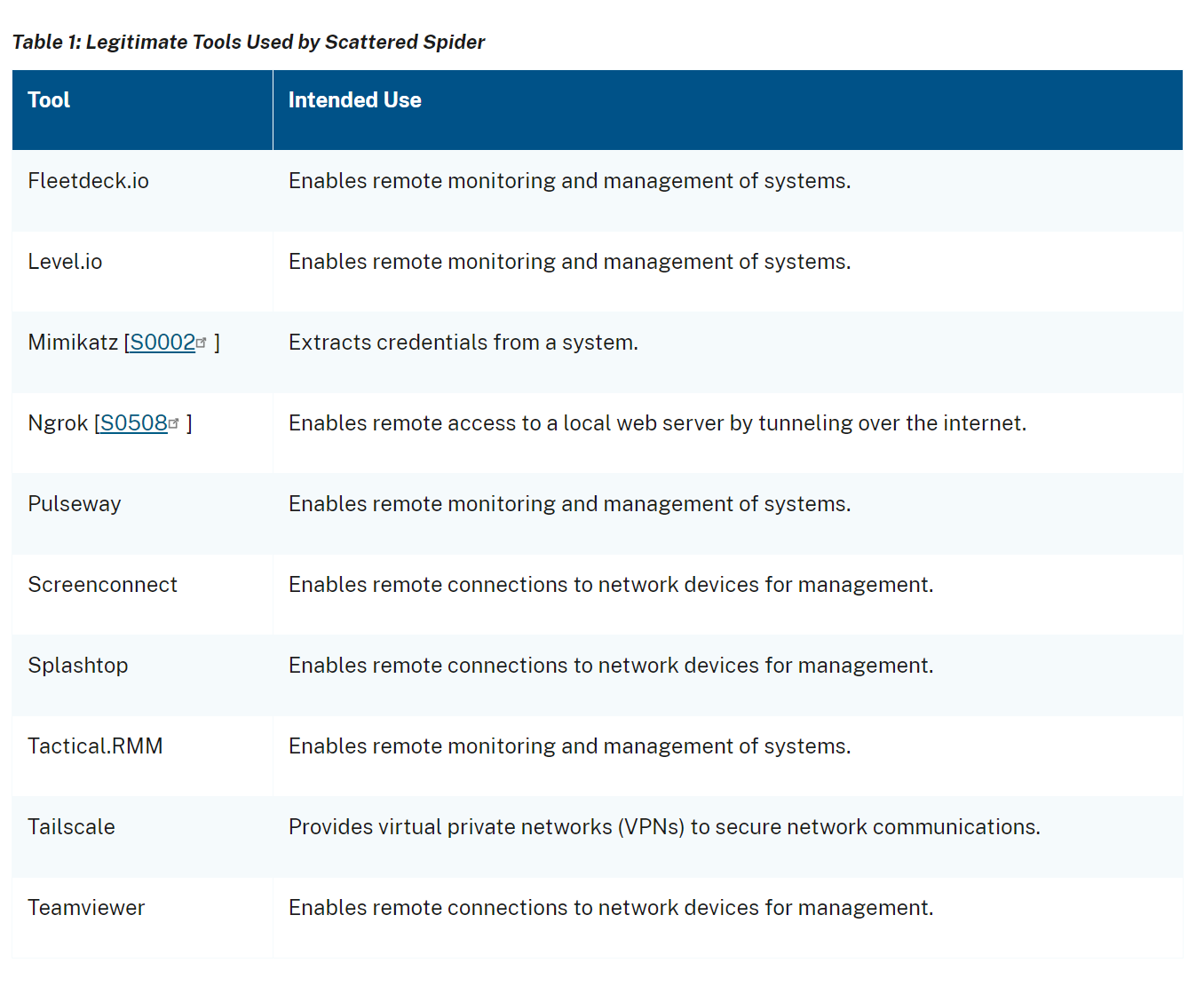
The advisory explains, “Scattered Spider threat actors have historically evaded detection on target networks by using living off the land techniques and allowlisted applications to navigate victim networks, as well as frequently modifying their TTPs. […]
“To determine if their activities have been uncovered and maintain persistence, Scattered Spider threat actors often search the victim’s Slack, Microsoft Teams and Microsoft Exchange online for emails [T1114] or conversations regarding the threat actor’s intrusion and any security response. The threat actors frequently join incident remediation and response calls and teleconferences, likely to identify how security teams are hunting them and proactively develop new avenues of intrusion in response to victim defenses. This is sometimes achieved by creating new identities in the environment [T1136] and is often upheld with fake social media profiles [T1585.001] to backstop newly created identities.” […]
“The FBI and CISA recommend organizations implement the mitigations below to improve your organization’s cybersecurity posture based on the threat actor activity and to reduce the risk of compromise by Scattered Spider threat actors. […]
- Implement application controls to manage and control execution of software, including allowlisting remote access programs. Application controls should prevent installation and execution of portable versions of unauthorized remote access and other software. […]
- Reduce threat of malicious actors using remote access tools by:
- Auditing remote access tools on your network to identify currently used and/or authorized software.
- Reviewing logs for execution of remote access software to detect abnormal use of programs running as a portable executable
- Using security software to detect instances of remote access software being loaded only in memory.
- Requiring authorized remote access solutions to be used only from within your network over approved remote access solutions, such as virtual private networks (VPNs) or virtual desktop interfaces (VDIs).
- Blocking both inbound and outbound connections on common remote access software ports and protocols at the network perimeter.
- Applying recommendations in the Guide to Securing Remote Access Software.
- Implementing FIDO/WebAuthn authentication or Public Key Infrastructure (PKI)-based MFA. These MFA implementations are resistant to phishing and not susceptible to push bombing or SIM swap attacks, which are techniques known to be used by Scattered Spider actors. See CISA’s fact sheet Implementing Phishing-Resistant MFA for more information.
- Strictly limit the use of Remote Desktop Protocol (RDP) and other remote desktop services. If RDP is necessary, rigorously apply best practices, for example:
- Audit the network for systems using RDP.
- Close unused RDP ports.
- Enforce account lockouts after a specified number of attempts.
- Apply phishing-resistant multifactor authentication (MFA).
- Log RDP login attempts.
In addition, the authoring authorities of this CISA recommend network defenders apply the following mitigations to limit potential adversarial use of common system and network discovery techniques, and to reduce the impact and risk of compromise by ransomware or data extortion actors: […]
- Implement application controls to manage and control execution of software, including allowlisting remote access programs. Application controls should prevent installation and execution of portable versions of unauthorized remote access and other software. […]
- Reduce threat of malicious actors using remote access tools by:
- Auditing remote access tools on your network to identify currently used and/or authorized software.
- Reviewing logs for execution of remote access software to detect abnormal use of programs running as a portable executable
- Using security software to detect instances of remote access software being loaded only in memory.
- Requiring authorized remote access solutions to be used only from within your network over approved remote access solutions, such as virtual private networks (VPNs) or virtual desktop interfaces (VDIs).
- Blocking both inbound and outbound connections on common remote access software ports and protocols at the network perimeter.
- Applying recommendations in the Guide to Securing Remote Access Software.
- Implementing FIDO/WebAuthn authentication or Public Key Infrastructure (PKI)-based MFA. These MFA implementations are resistant to phishing and not susceptible to push bombing or SIM swap attacks, which are techniques known to be used by Scattered Spider actors. See CISA’s fact sheet Implementing Phishing-Resistant MFA for more information.
- Strictly limit the use of Remote Desktop Protocol (RDP) and other remote desktop services. If RDP is necessary, rigorously apply best practices, for example:
- Audit the network for systems using RDP.
- Close unused RDP ports.
- Enforce account lockouts after a specified number of attempts.
- Apply phishing-resistant multifactor authentication (MFA).
- Log RDP login attempts.
In addition, the authoring authorities of this CISA recommend network defenders apply the following mitigations to limit potential adversarial use of common system and network discovery techniques, and to reduce the impact and risk of compromise by ransomware or data extortion actors:
- Implement a recovery plan to maintain and retain multiple copies of sensitive or proprietary data and servers in a physically separate, segmented and secure location (i.e., hard drive, storage device, the cloud).
- Maintain offline backups of data and regularly maintain backup and restoration (daily or weekly at minimum). By instituting this practice, an organization limits the severity of disruption to its business practices
- Require all accounts with password logins (e.g., service account, admin accounts and domain admin accounts) to comply with NIST’s standards for developing and managing password policies.
- Use longer passwords consisting of at least eight characters and no more than 64 characters in length
- Store passwords in hashed format using industry-recognized password managers.
- Add password user “salts” to shared login credentials.
- Avoid reusing passwords
- Implement multiple failed login attempt account lockouts
- Disable password “hints.”
- Refrain from requiring password changes more frequently than once per year.
Note: NIST guidance suggests favoring longer passwords instead of requiring regular and frequent password resets. Frequent password resets are more likely to result in users developing password “patterns” cyber criminals can easily decipher. - Require administrator credentials to install software.
- Require phishing-resistant multifactor authentication (MFA) for all services to the extent possible, particularly for webmail, virtual private networks (VPNs) and accounts that access critical systems
- Keep all operating systems, software and firmware up to date. Timely patching is one of the most efficient and cost-effective steps an organization can take to minimize its exposure to cybersecurity threats. Prioritize patching known exploited vulnerabilities in internet-facing systems
- Segment networks to prevent the spread of ransomware. Network segmentation can help prevent the spread of ransomware by controlling traffic flows between—and access to—various subnetworks and by restricting adversary lateral movement
- Identify, detect and investigate abnormal activity and potential traversal of the indicated ransomware with a networking monitoring tool. To aid in detecting the ransomware, implement a tool that logs and reports all network traffic and activity, including lateral movement, on a network. Endpoint detection and response (EDR) tools are particularly useful for detecting lateral connections as they have insight into common and uncommon network connections for each host
- Install, regularly update and enable real time detection for antivirus software on all hosts.
- Disable unused ports and protocols
- Consider adding an email banner to emails received from outside your organization
- Disable hyperlinks in received emails.
- Ensure all backup data is encrypted, immutable (i.e., ensure backup data cannot be altered or deleted), and covers the entire organization’s data infrastructure”
There is even more in the advisory, and it is direct, actionable advice for your information teams. If you don’t already, I suggest you subscribe to these FBI/CISA alerts. Even if Scatter Spider is not attacking your organization, they are an evolving case study and other hackers will try to mimic their TTPs.
To sign up for these CISA alerts, submit your email at this link:
https://public.govdelivery.com/accounts/USDHSCISA/subscriber/new





